Point Organization Corporation (A-GEL Gift Points) World's first* "Security Multiple Compound Patent Right Theory" license is now available. Ransomware, server attacks, etc. are defended 99% of the time and 0.3% or less probability of damage occurrence. Achieve "99% or more defense rate and 0.3% or less damage probability" with 73 attack indicators. Targeting "99% or more defense rate and 0.3% or less damage occurrence probability" for 73 attack indicators is possible. ~All-around security enhancement by adding APIs without changing the existing infrastructure
株式会社ポイント機構
The Point Organization, Inc. (Head Office: Sendagaya, Shibuya-ku, Tokyo; President: Yuki Takeuchi; hereinafter referred to as "the Company") has started to license "Vital Security Patent (Patent No. 7780682) and Sound General (Emergency Alert) Patent (Patent No. 7796450)" of the "Multiple Compound Patent Right Theory (hereinafter referred to as "the Theory"), which covers all security enhancement. (Patent No. 7796450)" of "Vital Security Patent (Patent No. 7780682)". Yuki Takeuchi, President and Representative Director of the Company, is currently working to obtain approximately 30 patents (including those planned, pending, and confirmed for acquisition) and to introduce a system using original coupons and original points for the customers (A-GEL system: a system that allows merchants to receive up to 40% of points for supporting their daily lives and business owners for free). We are developing a sales consulting company positioned to realize sales improvement and cost reduction for business owners by introducing the A-GEL Gift Point and A-GEL Gift Card system (post-paid success fee type) using original coupons and original points at zero yen. We came up with the idea of this new patent because we want to "eliminate various crimes," "create an environment where rescue and relief can be provided by automatically notifying and locating people in an emergency situation," "reduce the environment where people are saddened and hurt by the actions of others," "eliminate car theft, vandalism of unmanned stores, vandalism of vending machines," "reduce the number of people who are killed," and "reduce the number of people who are injured. We want to eliminate car theft, vandalism of unmanned stores, and vandalism of vending machines," and "We want to realize a future in which people of all walks of life can protect their safety, smiles, and happiness.
Video explaining the contents of the patents offered for license: https://youtu.be/hxV3rdUfklY?si=cpQgTatxBrvnanyo
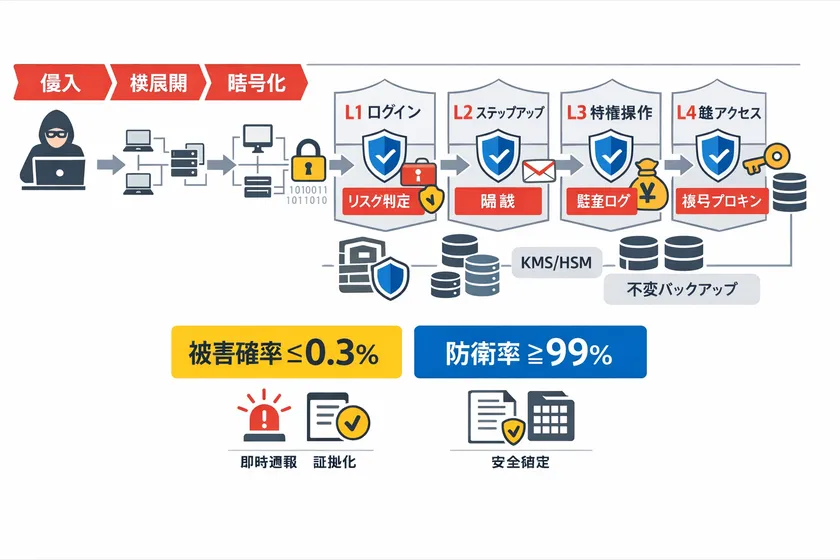
Image (1)
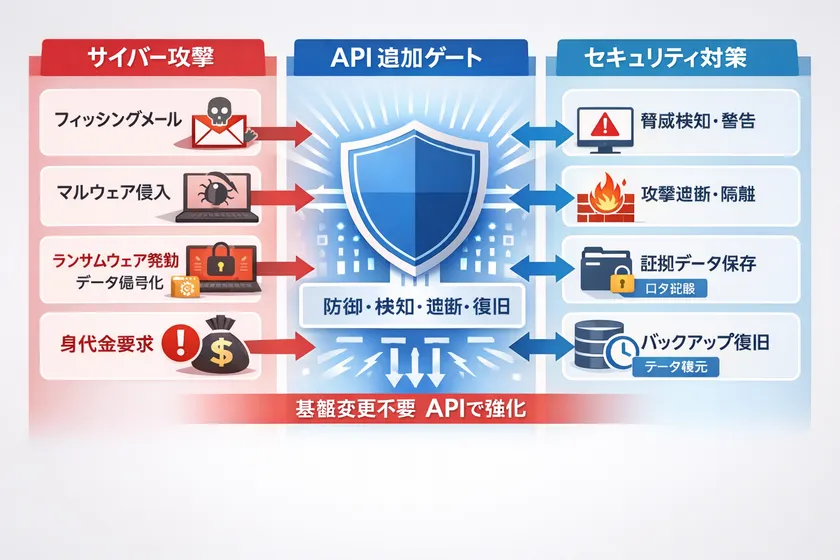
Image (2)
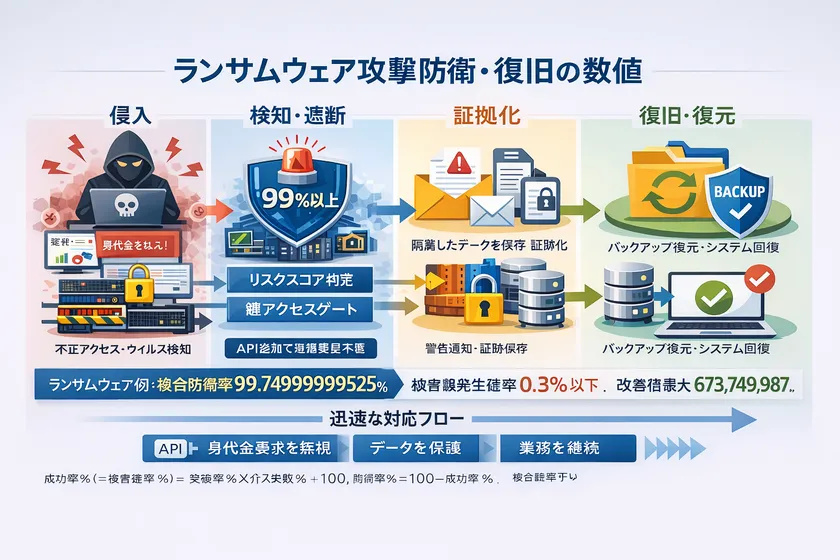
Image image (3)
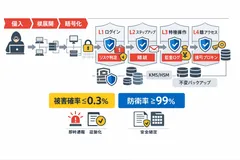
This theory organizes 73 types of attacks including ransomware, server attacks, spoofing, inducement, supply chain, internal fraud, AI abuse, etc., into categories A to J. The defense/defense/breakthrough/success rates (= damage probability) and improvement rates (multipliers) for conventional measures and when this theory is introduced (combined) are indexed in the same format. The Company has developed the following indexes in the same format.
Based on the above, we set the target indicators of "defense rate of 99% or more" and "damage occurrence probability of 0.3% or less" for all-round security enhancement by introducing this theory (assumed values based on "73 Attack Indicators List" prepared by us. (Assumptions and calculation formulas are specified in the Exhibit attached hereto.)
Definition of the values (Attachment 5: Original text of the calculation formulas)
Conventional success rate (= conventional damage probability %) = conventional breakthrough rate % x conventional intervention failure rate / 100, conventional defense rate (= conventional prevention rate % = conventional countermeasure rate % = conventional failure rate (result)%) = 100 - conventional success rate %. (Similarly, the combined side is also defined as combined success rate% (= combined damage probability%) = combined breakthrough rate% x combined intervention failure% / 100, combined defense rate% = 100 - combined success rate%).
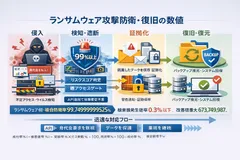
Furthermore, the improvement multiplier compared to conventional countermeasures reaches a maximum of 673,749,987,198.75 times in our comparison model, although it varies depending on the type of attack.
Background: Diverse Server Attacks Occur Every Year and Fragmentation of Countermeasures
In recent years, attacks targeting corporations, local governments, and infrastructure for daily life have become more diverse every year, expanding to include ransomware, intrusion/alteration, information leakage, internal fraud, spoofing, and AI exploitation. On the other hand, individual countermeasures alone tend to leave issues such as "operation based on the premise of a breach" (recovery, accountability, lack of evidence), and "omissions" occur due to the fragmentation of countermeasures. The number of attacks can be seen in the list of external damages (link below) (reference). 2.
The framework of this theory: "Stop x Inform x Leave" by integrating multiple patents
This theory integrates multiple patents to establish not only mere detection and notification, but also the following as a whole.
Stop: Preventing important operations from being executed or cancelled by conditions.
Notify: Automatic notification and alarm in the event of an abnormality.
Leave: Ensure a trail (evidence) against attacks and anomalies (assuming operation including tamper-resistance)
The contents of this theory are scheduled to be published in a media release around March. 3.
3. introduction features: phased introduction by adding APIs without changing the existing infrastructure
This license does not require a complete change of the existing system or server infrastructure, but can be introduced as an additional enhancement to the existing environment with an API.
Specifically, while maintaining the existing ID infrastructure, applications, and server configuration, "final judgment (permit/deny)" is added immediately before important operations (authentication, authorization, decryption, remittance, etc.), and any sign of abnormality is chained to block, notify, and document.
In addition, as shown in Exhibit 5, indicators (defense rate, breakthrough rate, success rate = damage probability, defense rate, etc.) are listed by attack, with assumptions (notification arrival rate, intervention success rate, etc.) and calculation formulas clarified.
4. 73 Attack Indicators (Example)
Our "List of Indicators for 73 Attacks" shows a parallel comparison of indicators for each attack between conventional countermeasures and those after the introduction of combined countermeasures.
Assumed indicators against ransomware (encryption and double threats) (example)
Ransomware (encryption/double threats)" is organized as a terminal attack (Category C), and the index after combined introduction is shown as: combined defense rate 99.7499999999525%, combined damage probability 0.250000000000475% (≤0.3%).
Assumed indicators for phishing (e-mail/contact application/fake website) (example)
Phishing is classified as Category A, and the following indicators are shown after the combined introduction: combined defense rate 99.9999999999985%, combined damage probability 0.000000000000015000000285%, and improvement factor of 261,333,328,368 times.
Examples of maximum improvement multipliers (our comparison model)
For some attacks in the physical/field area (Category I), an improvement factor of 673,749,987,198.75x is shown.
5. evidence (audit/trail) is assumed as part of the scope of rights
Attacks can include not only "intrusion and execution" but also concealment of evidence (e.g., deletion of logs) and audit evasion. This theory assumes that
This theory also considers evidence (e.g., evidence preservation, encrypted storage, etc.) as an important element, and aims to contribute to operational accountability and prevention of recurrence. 6.
Attachments (Appendix)
Attachment 1: Description and License Agreement
Attachment 2: Draft of media release (detailed version)
Attachment 3: Comparison of values when introducing conventional vs. multiple compound patent rights (yellow part)
Attachment 4: Comparison of figures when introducing conventional vs. multiple compound patent theory (colored part)
Attachment 5: Formulas for calculating comparative figures (including assumptions and attack model definitions)
Notes
*"World Beginner Level" is our positioning.
*"Defense Ratio," "Damage Incidence Probability," and "Improvement Multiplier" are AI simulation calculations. They are assumed values based on the assumptions (notification arrival rate, intervention success rate, etc.) and calculation formulas shown in Exhibit 5, and may vary depending on the scope of implementation, operational conditions, scope of collaboration, and design method. The license agreement also includes the provision of such know-how.
The specifics of this theory will be made public in a media release around March.
Comment by Yuki Takeuchi, inventor and inventor
I would like to improve and solve various social problems through various projects and inventions, and bring smiles to the faces of Japan in the future through security and safety.
Yuki Takeuchi is currently developing the "A-GEL Gift Point" and "A-GEL Gift Card" services, which allow merchants to give up to 40% back in points free of charge, to support people's lives and business owners through the use of patented rights. A-GEL Gift Point" and "A-GEL Gift Card" services, which allow merchants to give up to 40% of their points for free.
- Category:
- Corporate Trends
- Genres:
- Technology General Business Economy(Japan)